I'm going to test this out. I've heard of it but never knew what all it was intended to do.
Saturday, September 24, 2011
Friday, September 23, 2011
Projects
The following are the chapter objectives from Cisco Exploration I/Cisco Academy's online materials [ISBN-13: 978-1587132087].
If you have a project due on a specific layer of the OSI model, you may find it helpful to use the points expressed for that chapter as a starting point for your Powerpoint slides.
Good luck, everyone.
Chapter Objectives for Network Fundamentals CCNA Exploration v4
Chapter 1 Living in a Network-Centric World
How do networks impact our daily lives?
What is the role of data networking in the human network?
What are the key components of a data network?
What are the opportunities and challenges posed by converged networks?
What are the characteristics of network architectures?
Chapter 2 Communicating over the Network
What is the structure of a network, including devices and media necessary for communications?
What function do protocols perform in network communications?
What are the advantages of using a layered model to describe network functionality?
What is the role of each layer in the OSI network model and the TCP/IP network model?
What is the importance of addressing and naming schemes in network communications?
Chapter 3 Application Layer Functionality and Protocols
How do the functions of the three upper OSI model layers provide network services to end-user applications?
How do the TCP/IP application layer protocols provide the services specified by the upper layers of the OSI model?
How do people use the application layer to communicate across the information network?
What are the functions of well-known TCP/IP applications, such as the World Wide Web and e-mail, and their related services (HTTP, DNS, DHCP, STMP/POP, and Telnet)?
What are the file-sharing processes that use peer-to-peer applications and the Gnutella protocol?
How do protocols ensure that services running on one kind of device can send to and receive from many different network devices?
How can you use network analysis tools to examine and explain how common user applications work?
Chapter 4 OSI Transport Layer
Why is there a need for the transport layer?
What is the role of the transport layer as it provides the end-to-end transfer of data between applications?
What is the role of two TCP/IP transport layer protocols: TCP and UDP?
How do the key functions of the transport layer protocol, including reliability, port addressing, and segmentation, work?
How do TCP and UDP handle the key functions?
When is it appropriate to use TCP or UDP, and what are some examples of applications that use each protocol?
Chapter 5 OSI Network Layer
What is the method described by the network layer for routing packets from a device on one network to a device on a different network?
How does the Internet Protocol (IP) work at the network layer to provide connectionless, best-effort service to the upper layers of the OSI model?
How are devices grouped into physical and logical networks?
How do the hierarchical addresses of devices allow communication between networks?
How do routers use next-hop addresses to select a path for packets to reach their destination?
How do routers forward packets?
Chapter 6 Addressing the Network: IPv4
What type of addressing structure does IPv4 use?
What is the 8-bit binary equivalent of a given decimal number?
What is the decimal equivalent of a given 8-bit binary number?
What type of address is a given IPv4 address, and how is it used in a network?
How do administrators assign addresses within networks?
How are addresses assigned by ISPs?
What is the network portion of the host address?
What is the role of the subnet mask in dividing networks?
What are the appropriate addressing components for IPv4, given addressing design criteria?
How do you use testing utilities to verify and test network connectivity and operational status of the IP stack on a host?
Chapter 7 OSI Data Link Layer
What is the role of data link layer protocols in data transmission?
How does the data link layer prepare data for transmission on network media?
How do the types of MAC methods operate?
What are several common logical network topologies?
How does the logical topology determine the MAC method for a type of network?
What is the purpose of encapsulating packets into frames to facilitate media access?
What are the purposes of the Layer 2 frame structure?
What are the generic fields of a Layer 2 frame?
What is the role of the key frame header and trailer fields, including addressing, QoS, type of protocol, and Frame Check Sequence?
Chapter 8 OSI Physical Layer
What role do the physical layer protocols and services play in supporting communication across data networks?
What is the purpose of physical layer signaling and encoding used in networks?
How do signals represent bits as a frame as data is transported across the local media?
What are the basic characteristics of copper, fiber, and wireless network media?
What are common implementations of copper, fiber, and wireless media in networks?
Chapter 9 Ethernet
How did Ethernet evolve?
What are the purposes of the fields of the Ethernet frame?
What are the function and characteristics of the media access control method used by Ethernet protocol?
What are the physical and data link layer features of Ethernet?
How are Ethernet hubs and switches different?
What is the purpose of Address Resolution Protocol (ARP) and how does it operate?
Chapter 10 Planning and Cabling Networks
What basic network media is required to make a LAN connection?
What are the types of connections used for intermediate and end-device connectivity in a LAN?
What are the pinout configurations for straight-through and crossover cables?
What are the different cabling types, standards, and ports used in WAN connections?
What is the role of device connections management when using Cisco equipment?
How do you design an addressing scheme for an internetwork and assign ranges for hosts, network devices, and the router interface?
Why is network design so important?
Chapter 11 Configuring and Testing Your Network
What is the role of the IOS?
What is the purpose of a configuration file?
What are the classes of devices that have the IOS embedded?
What are the factors contributing to the set of IOS commands available to a device?
What are the IOS modes of operation?
What are the basic IOS commands?
How are the basic show commands used and why?
If you have a project due on a specific layer of the OSI model, you may find it helpful to use the points expressed for that chapter as a starting point for your Powerpoint slides.
Good luck, everyone.
Chapter Objectives for Network Fundamentals CCNA Exploration v4
Chapter 1 Living in a Network-Centric World
How do networks impact our daily lives?
What is the role of data networking in the human network?
What are the key components of a data network?
What are the opportunities and challenges posed by converged networks?
What are the characteristics of network architectures?
Chapter 2 Communicating over the Network
What is the structure of a network, including devices and media necessary for communications?
What function do protocols perform in network communications?
What are the advantages of using a layered model to describe network functionality?
What is the role of each layer in the OSI network model and the TCP/IP network model?
What is the importance of addressing and naming schemes in network communications?
Chapter 3 Application Layer Functionality and Protocols
How do the functions of the three upper OSI model layers provide network services to end-user applications?
How do the TCP/IP application layer protocols provide the services specified by the upper layers of the OSI model?
How do people use the application layer to communicate across the information network?
What are the functions of well-known TCP/IP applications, such as the World Wide Web and e-mail, and their related services (HTTP, DNS, DHCP, STMP/POP, and Telnet)?
What are the file-sharing processes that use peer-to-peer applications and the Gnutella protocol?
How do protocols ensure that services running on one kind of device can send to and receive from many different network devices?
How can you use network analysis tools to examine and explain how common user applications work?
Chapter 4 OSI Transport Layer
Why is there a need for the transport layer?
What is the role of the transport layer as it provides the end-to-end transfer of data between applications?
What is the role of two TCP/IP transport layer protocols: TCP and UDP?
How do the key functions of the transport layer protocol, including reliability, port addressing, and segmentation, work?
How do TCP and UDP handle the key functions?
When is it appropriate to use TCP or UDP, and what are some examples of applications that use each protocol?
Chapter 5 OSI Network Layer
What is the method described by the network layer for routing packets from a device on one network to a device on a different network?
How does the Internet Protocol (IP) work at the network layer to provide connectionless, best-effort service to the upper layers of the OSI model?
How are devices grouped into physical and logical networks?
How do the hierarchical addresses of devices allow communication between networks?
How do routers use next-hop addresses to select a path for packets to reach their destination?
How do routers forward packets?
Chapter 6 Addressing the Network: IPv4
What type of addressing structure does IPv4 use?
What is the 8-bit binary equivalent of a given decimal number?
What is the decimal equivalent of a given 8-bit binary number?
What type of address is a given IPv4 address, and how is it used in a network?
How do administrators assign addresses within networks?
How are addresses assigned by ISPs?
What is the network portion of the host address?
What is the role of the subnet mask in dividing networks?
What are the appropriate addressing components for IPv4, given addressing design criteria?
How do you use testing utilities to verify and test network connectivity and operational status of the IP stack on a host?
Chapter 7 OSI Data Link Layer
What is the role of data link layer protocols in data transmission?
How does the data link layer prepare data for transmission on network media?
How do the types of MAC methods operate?
What are several common logical network topologies?
How does the logical topology determine the MAC method for a type of network?
What is the purpose of encapsulating packets into frames to facilitate media access?
What are the purposes of the Layer 2 frame structure?
What are the generic fields of a Layer 2 frame?
What is the role of the key frame header and trailer fields, including addressing, QoS, type of protocol, and Frame Check Sequence?
Chapter 8 OSI Physical Layer
What role do the physical layer protocols and services play in supporting communication across data networks?
What is the purpose of physical layer signaling and encoding used in networks?
How do signals represent bits as a frame as data is transported across the local media?
What are the basic characteristics of copper, fiber, and wireless network media?
What are common implementations of copper, fiber, and wireless media in networks?
Chapter 9 Ethernet
How did Ethernet evolve?
What are the purposes of the fields of the Ethernet frame?
What are the function and characteristics of the media access control method used by Ethernet protocol?
What are the physical and data link layer features of Ethernet?
How are Ethernet hubs and switches different?
What is the purpose of Address Resolution Protocol (ARP) and how does it operate?
Chapter 10 Planning and Cabling Networks
What basic network media is required to make a LAN connection?
What are the types of connections used for intermediate and end-device connectivity in a LAN?
What are the pinout configurations for straight-through and crossover cables?
What are the different cabling types, standards, and ports used in WAN connections?
What is the role of device connections management when using Cisco equipment?
How do you design an addressing scheme for an internetwork and assign ranges for hosts, network devices, and the router interface?
Why is network design so important?
Chapter 11 Configuring and Testing Your Network
What is the role of the IOS?
What is the purpose of a configuration file?
What are the classes of devices that have the IOS embedded?
What are the factors contributing to the set of IOS commands available to a device?
What are the IOS modes of operation?
What are the basic IOS commands?
How are the basic show commands used and why?
Saturday, September 17, 2011
I know this isn't computer-related but...
...It's my blog and I can do what I want. What I want to do right now is show you all the only import car I would buy.
Thursday, September 15, 2011
Sorry, Everyone!
To those of you who are waiting on the "Test Hardware" portion of the website, I apologize for the delay. I'm really trying to set some time aside this weekend to at least get The Rundown posted for that page. Hopefully, work and studies permitting, I can make that happen.
Thanks for your patience and, as always, feel free to send your questions to admin@remedycomputing.com. A specific question probably has a specific answer, which is much faster for me to respond to than trying to write something that will apply to all people.
PS
A new batch of stickers is ready so if you'd like to help out, let me know and we'll get you set up with a stack. Thanks!
Thanks for your patience and, as always, feel free to send your questions to admin@remedycomputing.com. A specific question probably has a specific answer, which is much faster for me to respond to than trying to write something that will apply to all people.
PS
A new batch of stickers is ready so if you'd like to help out, let me know and we'll get you set up with a stack. Thanks!
Wednesday, September 14, 2011
IPv4 Subnetting Info
I found a page that explains subnetting in about the easiest way possible, I hope it helps everyone.
http://www.pantz.org/software/tcpip/subnetchart.html
http://www.pantz.org/software/tcpip/subnetchart.html
Monday, September 12, 2011
IPv4 Address Classes
Here's a chart to show you why the IP classes are broken up the way they are so you can quickly identify them.
As shown above, Class A addresses are those in which the first octet's value ranges between 1 and 127. The key to remembering this is that numbers from 1-127 will always have the first bit turned off [or 0xxxxxxx] when expressed in binary form. 1-127 can also be expressed as 00000001-01111111. It should also be noted that any 127.x.x.x address is a "loopback" address used only for testing purposes and will never be assigned to a network device, so while Class A addresses technically range from 1-127, some sources may imply that the class spans from 1-126.
Class B addresses will always have the first bit on and second bit off [or 10xxxxxx] in the first octet. This means everything between 128 [10000000] and 191 [10111111] would be considered a Class B address.
Class C and the consecutive classes D and E will follow suit by adding another on-bit in front each time you progress a tier. For example, Class C addresses will start with 110xxxxx, Class D with 1110xxxx and Class E begins with 1111xxxx and drops the off-bit we were carrying so that we can close the rest of the 0-255 spectrum. So, Class C addresses range from 192 [11000000] to 223 [11011111].
The Classes also define how many bytes or octets are used to express the network ID and how many are used for the host ID. In short, Class A addresses use the first octet for the network ID and the remaining three octets are used to distinguish the host ID. NETWORK.HOST.HOST.HOST
Class B uses the first and second octet to outline the network ID, leaving the third and fourth octets for the host ID. This results in a greater number of possible networks when compared to Class A, but with fewer hosts on each of those networks. NETWORK.NETWORK.HOST.HOST
The pattern continues with Class C, using the beginning three octets for the network ID and the final octet for host IDs, resulting in far fewer possible hosts. This concept is illustrated in the picture below. NETWORK.NETWORK.NETWORK.HOST
I found that picture in an old networking folder on my computer but I can't find the source to site it. I will gladly take it down if requested by the owner. I can be reached at admin@remedycomputing.com.
I will write more later on easily converting numbers between dotted-decimal form [172.16.30.56], binary form [10101100.00010000.00011110.00111000] and hexadecimal form [AC.10.1E.38].
As shown above, Class A addresses are those in which the first octet's value ranges between 1 and 127. The key to remembering this is that numbers from 1-127 will always have the first bit turned off [or 0xxxxxxx] when expressed in binary form. 1-127 can also be expressed as 00000001-01111111. It should also be noted that any 127.x.x.x address is a "loopback" address used only for testing purposes and will never be assigned to a network device, so while Class A addresses technically range from 1-127, some sources may imply that the class spans from 1-126.
Class B addresses will always have the first bit on and second bit off [or 10xxxxxx] in the first octet. This means everything between 128 [10000000] and 191 [10111111] would be considered a Class B address.
Class C and the consecutive classes D and E will follow suit by adding another on-bit in front each time you progress a tier. For example, Class C addresses will start with 110xxxxx, Class D with 1110xxxx and Class E begins with 1111xxxx and drops the off-bit we were carrying so that we can close the rest of the 0-255 spectrum. So, Class C addresses range from 192 [11000000] to 223 [11011111].
The Classes also define how many bytes or octets are used to express the network ID and how many are used for the host ID. In short, Class A addresses use the first octet for the network ID and the remaining three octets are used to distinguish the host ID. NETWORK.HOST.HOST.HOST
Class B uses the first and second octet to outline the network ID, leaving the third and fourth octets for the host ID. This results in a greater number of possible networks when compared to Class A, but with fewer hosts on each of those networks. NETWORK.NETWORK.HOST.HOST
The pattern continues with Class C, using the beginning three octets for the network ID and the final octet for host IDs, resulting in far fewer possible hosts. This concept is illustrated in the picture below. NETWORK.NETWORK.NETWORK.HOST
I found that picture in an old networking folder on my computer but I can't find the source to site it. I will gladly take it down if requested by the owner. I can be reached at admin@remedycomputing.com.
I will write more later on easily converting numbers between dotted-decimal form [172.16.30.56], binary form [10101100.00010000.00011110.00111000] and hexadecimal form [AC.10.1E.38].
Sunday, September 11, 2011
September 11th, 2001
Saturday, September 10, 2011
More stickers found
A few more pictures received today...
Stairwell - Katy, Texas
LSC - Cypress, Texas
LSC - Cypress, Texas
LSC - Cypress, Texas
New batches of stickers will be ready approximately Wednesday.
LSC - Cypress, Texas
LSC - Cypress, Texas
LSC - Cypress, Texas
New batches of stickers will be ready approximately Wednesday.
Friday, September 9, 2011
Stickers
So I have pictures from friends that have placed or come across stickers for RemedyComputing.com website somewhere and I think I'm going to start posting them. Thanks to everyone that has helped so far and to everyone who is waiting on their batch of stickers.
If you see a sticker that you know is for RC, take a picture and email it to me. Be sure to include where the picture was taken. We're going to start a game, based on best/highest exposure/most unique placement, as soon as we fully outline the rules.
If you would like stickers to spread the word, let me know and I'll see if we can't get you set up with a stack.
Without further ado...
Chuy's - Katy, Texas
Buffalo Wild Wings - Katy, Texas
McDonald's - Katy, Texas
If you see a sticker that you know is for RC, take a picture and email it to me. Be sure to include where the picture was taken. We're going to start a game, based on best/highest exposure/most unique placement, as soon as we fully outline the rules.
If you would like stickers to spread the word, let me know and I'll see if we can't get you set up with a stack.
Without further ado...
Buffalo Wild Wings - Katy, Texas
McDonald's - Katy, Texas
Thursday, September 8, 2011
TCP/UDP Port Numbers
For reference, I found a full list of TCP and UDP ports on Wikipedia. The problem is that it's a FULL list so it's probably only good for looking specific ports up. I'm going to try to find or make a list of port names, numbers and functions that only includes entries relative to the CCNA exam.
In the mean time, below is the full list:
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
Here's an article I found referencing a lot of ports used in Cisco routing:
http://www.techrepublic.com/blog/networking/why-you-need-to-know-cisco-ios-acl-port-numbers/326
In the mean time, below is the full list:
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
Here's an article I found referencing a lot of ports used in Cisco routing:
http://www.techrepublic.com/blog/networking/why-you-need-to-know-cisco-ios-acl-port-numbers/326
CCNA Exam Objectives
With as quickly as we move through these course materials, I think it could be easy get overwhelmed by the amount of information you're expected to memorize. Something I found when I got my CompTIA certifications is that, in these books and other documentation, there are ofter details emphasized that aren't necessarily relevant to the exam objectives. Some points made might aid in understanding a concept you will be tested on but may not be pertinent to the exam itself.
I have spent countless hours trying to cram port numbers, protocols, obsolete media attributes, commands, etc into my brain in preparation for one of these certification exams to later find that half of these weren't even possible test questions on my exam. Considering this, I suggest everyone interested in taking their CCNA or any other certification exam regularly read their exam objectives, that way you know what to focus on.
Below are links to the 640-802 [current CCNA] exam objectives. Print them, keep them with you, look over them daily and especially before you do any reading/studying. Eventually, as you read each bullet, answers with come to mind automatically. Both lists are broken up into 8 categories with bullets marking subpoints or specific questions in each primary category. It seems like they're listed by the order Cisco wants you to learn the objectives in, meaning the categories labeled "Describe how a network works" and "Configure, verify and troubleshoot a switch with VLANs and interswitch communications" would be the focus of the first quarter Cisco Exploration class. I could be wrong about that, though. In any case, here are the links.
The first seems to be a public page:
http://www.cisco.com/web/learning/le3/current_exams/640-802.html
The second one asked me to log into my Cisco account and seems to have the same information but with a few more related links posted:
https://learningnetwork.cisco.com/docs/DOC-4976
That's all for now, good luck!
I have spent countless hours trying to cram port numbers, protocols, obsolete media attributes, commands, etc into my brain in preparation for one of these certification exams to later find that half of these weren't even possible test questions on my exam. Considering this, I suggest everyone interested in taking their CCNA or any other certification exam regularly read their exam objectives, that way you know what to focus on.
Below are links to the 640-802 [current CCNA] exam objectives. Print them, keep them with you, look over them daily and especially before you do any reading/studying. Eventually, as you read each bullet, answers with come to mind automatically. Both lists are broken up into 8 categories with bullets marking subpoints or specific questions in each primary category. It seems like they're listed by the order Cisco wants you to learn the objectives in, meaning the categories labeled "Describe how a network works" and "Configure, verify and troubleshoot a switch with VLANs and interswitch communications" would be the focus of the first quarter Cisco Exploration class. I could be wrong about that, though. In any case, here are the links.
The first seems to be a public page:
http://www.cisco.com/web/learning/le3/current_exams/640-802.html
The second one asked me to log into my Cisco account and seems to have the same information but with a few more related links posted:
https://learningnetwork.cisco.com/docs/DOC-4976
That's all for now, good luck!
Wednesday, September 7, 2011
Tuesday, September 6, 2011
Interesting Lifehacker Articles
I have a few friends that run into issues when "building" their "hackintoshs" and some other that may be interested in making their first. This link might help.
http://lifehacker.com/5837615/how-do-i-choose-the-right-hardware-when-building-a-hackintosh
Another one for those of you who can't help but mod everything.
http://lifehacker.com/5837610/combine-a-ps3-and-an-xbox-360-in-one-computer-case-for-the-ultimate-gaming-machine
And one for those going back to school or, in my case, those of us just starting out with their Cisco training.
http://lifehacker.com/back-to-work/
http://lifehacker.com/5837615/how-do-i-choose-the-right-hardware-when-building-a-hackintosh
Another one for those of you who can't help but mod everything.
http://lifehacker.com/5837610/combine-a-ps3-and-an-xbox-360-in-one-computer-case-for-the-ultimate-gaming-machine
And one for those going back to school or, in my case, those of us just starting out with their Cisco training.
http://lifehacker.com/back-to-work/
RemedyComputing.com is 1 today!
While this blog may only be a couple days old, RemedyComputing.com turned 1 today!
Monday, September 5, 2011
Cisco Academy - Chapter 2
While looking through Chapter 2 of the course materials, there were a few points of interest that I wrote down for quick reference. They might be worth a second look.
cisco.netacad.net
2.3.4.1 - The Interaction of Protocols
2.4.4.1 - The Communication Process
2.4.6.1 - The Sending and Receiving Process
2.7.1.2 - Question 6, Postal Metaphor for Encapsulation
cisco.netacad.net
2.3.4.1 - The Interaction of Protocols
2.4.4.1 - The Communication Process
2.4.6.1 - The Sending and Receiving Process
2.7.1.2 - Question 6, Postal Metaphor for Encapsulation
Networking Acronyms
I found a list of networking acronyms and thought it would be helpful to everyone interested in or currently studying any type of networking.
--- A ---
ABM - Asynchronous Balanced Mode
ABR - Available Bit Rate
ACK - Acknowledgement (network related)
ACS - Access Control System
AD - Active Directory
ADN - Advanced Digital Network
aDSL - Asynchronous Digital Subscriber Line
AFP - AppleTalk Filing Protocol
AMP - Adapter Management Protocol
ANSI - American National Standards Institute
APPN - Advanced Peer to Peer Networking
ARP - Address Resolution Protocol
ARPAnet - Advanced Research Project Agency Network
ASBR - Autonomous System Boundary Router
ASCII - American Standard Code for Information Interchange
ASIC - Application Specific Integrated Circuit
ATM - Asynchronous Transfer Mode
AUI - Attachment Unit Interface
--- B ---
B2B - Business to Business
BECN - Backward Explicit Congestion Notification
BER - Bit Error Rate
BGP - Border Gateway Protocol
BIGA - Bus Interface Gate Array
BISDN - Broadband Integrated Services Digital Network
--- C ---
CAN - Campus Area Network
CCITT - Consultative Committee for International Telegraph and Telephone
CCS - Common Channel Signaling
CSS - Cascading Style Sheets
CDDI - Copper Distributed Data Interface
CGI - Common Gateway Interface
CICS - Customer Information Control System
CIDR - Classless Inter-Domain Routing
CIR - Commited Information Rate
CLNP - Connectionless Network Protocol
CONS - Connection Oriented Network Service
COSP - Connection Oriented Session Protocol
CSMA - Carrier-Sense Multiple Access
CSMA/CD - CSMA with Collision Detection
CSU/DSU - Channel Service Unit/Data Service Unit
--- D ---
DACS - Digital Access Cross-connected System
DAP - Directory Access Protocol
DCE - Data Communications Equipment
DDS - Digital Data Storage
DECNet - Digital Equipment Corporation Network
DHCP - Dynamic Host Configuration Protocol
DLC - Data Link Control
DLCI - Data Link Connection Identifier
DNS - Domain Name Service
DSL - Digital Subscriber Line
DVMRP - Distance-Vector Multicast Routing Protocol
--- E ---
EBCDIC - Extended Binary Coded Decimal Interchange Code
EDI - Electronic Data Interchange
EGP - Exterior Gateway Protocol
--- F ---
FDDI - Fibre Distributed Data Interface
FOIRL - Fibre Optic Inter-Repeater Link
FSP - File Service Protocol
FTP - File Transfer Protocol
--- G ---
GGP - Gateway to Gateway Protocol
GID - Global Information Distribution
GNS - Get Nearest Server
--- H ---
HSSI - High-Speed Serial Interface
HTML - HyperText Markup Language
HTTP - Hypertext Transfer Protocol
HTTPS - Hypertext Transfer Protocol Secure
--- I ---
IANA - Internet Assigned Numbers Authority
IAP - Internet Access Provider
IAB - Internet Architecture Board
ICMP - Internet Control Message Protocol
IDRP - Inter-Domain Routing Protocol
IEEE - Institute of Electrical and Electronics Engineers
IESG - Internet Engineering Steering Group
IETF - Internet Engineering Task Force
IGMP - Internet Group Management Protocol
IGP - Interior Gateway Protocol
InARP - Inverse Address Resolution Protocol
IP - Internet Protocol
IPX - Intergrated Packet Exchange
IPX/SPX - Intergrated Packet Exchange/Sequenced Packet Exchange
IRC - Internet Relay Chat
IRTF - Internet Research Task Force
ISDN - Integrated Services Digital Network
ISO - International Standards Organization
ISP - Internet Service Provider
IDSL - ISDN Digital Subscriber Line
IMAP - Internet Message Access Protocol
ISDN - Integrated Services Digital Network
--- J ---
JUNET - Japan UNIX Network
--- K ---
Kbps - Kilobits Per Second
KBps - KiloBytes per second
--- L ---
LAN - Local Area Network
LANE - Local Area Network Emulation
LDAP - Lightweight Directory Access Protocol
LLC - Logical Link Control
--- M ---
MAC - Media Access Control
MAN - Metropolitan Area Network
MAU - Multistation Access Unit
MBps - Megabytes Per Second
Mbps - Megabits Per Second
MIB - Management Information Base
MIME - Multiple Internet Mail Extensions
Modem - Modulate/Demodulate
MRU - Maximum Receive Unit
MTU - Maximum Transmissionn Agent
--- N ---
NAS - Network Attached Storage
NAT - Network Address Translation
NCP - Netware Core Protocol
NDIS - Network Driver Interface Specification
NDP - Neighbor Discovery Protocol
NDS - Novell Directory Services
NetBEUI - NetBIOS Extended User Interface
NetBIOS - Network Basic Input/Output System
NFS - Network File System
NIC - Network Interface Card
NNTP - Network News Transfer Protocol
NTP - Network Time Protocol
NVT - Network Virtual Terminal
--- O ---
ODI - Open Data-link Interface
OSI - Open System Interconnect
OSPF - Open Shortest Path First
--- P ---
P2P - Peer to Peer
PAD - Packet Assembler/Disassembler
PAN - Personal Area Network
PAT - Port Address Translation
Pb - Peta byte
PDU - Protocol Data Unit
PEP - Packet Exchange Protocol
PING - Packet InterNet Groper
POP - Post Office Protocol
POTS - Plain Old Telephone System
PPP - Point to Point Protocol
PPPoA - Point-to-Point Protocol over ATM
PPPoE - Point-to-Point Protocol over Ethernet
PPTP - Point to Point Tunneling Protocol
PSDN - Packet Switched Data Network
PSTN - Public Switched Telephone Network
PVC - Permanent Virtual Circuit
--- Q ---
QoS - Quality of Service
QoSP - Quality of Service Parameters
--- R ---
RARP - Reverse Address Resolution Protocol
RBCS - Remote Boot and Configuration Service
RFC - Request for Comment
RIP - Routing Information Protocol
RPC - Remote Procedure Call
--- S ---
SAN - Storage Area Network
SATAN - Security Analysis Tool for Auditing Networks
SLIP - Serial Line Internet Protocol
SMTP - Simple Mail Transfer Protocol
S/N - Subnet
SNA - Systems Network Architechture
SNAP - Sub-Network Access Protocol
SNMP - Simple Network Management Protocol
SNTP - Simple Network Time Protocol
SPX - Sequenced Packet Exchange
SQL - Structure Query Language
STP - Shieled Twisted Pair
SSH - Secure Shell
SSL - Secure Socket Layer
SVC - Switched Virtual Circuit
SWAT - Samba Administration Tool
--- T ---
TB - Terabytes
TBps - Terabytes per second
Tbps - Terabits per second
TCP - Transmission Control Protocol
TCP/IP - Transmission Control Protocol/Internet Protocol
TFTP - Trivial File Transfer Protocol
TOS - Type Of Service
TTL - Time To Live
--- U ---
UDLC - Universal Data Link Control
UDP - User Datagram Protocol
UNC - Universal Naming Convention
URL - Uniform Resource Locator
UTP - Unshieled Twisted Pair
UUEncode - Unix to Unix Encoding
--- V ---
VBR - Variable Bit Rate
VPC - Virtual Path Connection
VPN - Virtual Private Network
--- W ---
WAN - Wide Area Network
WANG - Wide Area Network Group
WINS - Windows Internet Naming Service
WLAN - Wireless Local Area Network
--- X ---
XDR - External Data Representation
xDSL - Extended Digital Subscriber Line
XML - Extensible Markup Language
XSL - Extensible Stylesheet Language
XSML - Extensible Stylesheet Markup Language
--- Y ---
--- Z ---
ZCS - Zero Code Suppression
^ The above information was copied from http://www.xtremetek.com/info/index.php?id=2&page=1#o
If you happen to notice one missing, please email it to me at Admin@remedycomputing.com
--- A ---
ABM - Asynchronous Balanced Mode
ABR - Available Bit Rate
ACK - Acknowledgement (network related)
ACS - Access Control System
AD - Active Directory
ADN - Advanced Digital Network
aDSL - Asynchronous Digital Subscriber Line
AFP - AppleTalk Filing Protocol
AMP - Adapter Management Protocol
ANSI - American National Standards Institute
APPN - Advanced Peer to Peer Networking
ARP - Address Resolution Protocol
ARPAnet - Advanced Research Project Agency Network
ASBR - Autonomous System Boundary Router
ASCII - American Standard Code for Information Interchange
ASIC - Application Specific Integrated Circuit
ATM - Asynchronous Transfer Mode
AUI - Attachment Unit Interface
--- B ---
B2B - Business to Business
BECN - Backward Explicit Congestion Notification
BER - Bit Error Rate
BGP - Border Gateway Protocol
BIGA - Bus Interface Gate Array
BISDN - Broadband Integrated Services Digital Network
--- C ---
CAN - Campus Area Network
CCITT - Consultative Committee for International Telegraph and Telephone
CCS - Common Channel Signaling
CSS - Cascading Style Sheets
CDDI - Copper Distributed Data Interface
CGI - Common Gateway Interface
CICS - Customer Information Control System
CIDR - Classless Inter-Domain Routing
CIR - Commited Information Rate
CLNP - Connectionless Network Protocol
CONS - Connection Oriented Network Service
COSP - Connection Oriented Session Protocol
CSMA - Carrier-Sense Multiple Access
CSMA/CD - CSMA with Collision Detection
CSU/DSU - Channel Service Unit/Data Service Unit
--- D ---
DACS - Digital Access Cross-connected System
DAP - Directory Access Protocol
DCE - Data Communications Equipment
DDS - Digital Data Storage
DECNet - Digital Equipment Corporation Network
DHCP - Dynamic Host Configuration Protocol
DLC - Data Link Control
DLCI - Data Link Connection Identifier
DNS - Domain Name Service
DSL - Digital Subscriber Line
DVMRP - Distance-Vector Multicast Routing Protocol
--- E ---
EBCDIC - Extended Binary Coded Decimal Interchange Code
EDI - Electronic Data Interchange
EGP - Exterior Gateway Protocol
--- F ---
FDDI - Fibre Distributed Data Interface
FOIRL - Fibre Optic Inter-Repeater Link
FSP - File Service Protocol
FTP - File Transfer Protocol
--- G ---
GGP - Gateway to Gateway Protocol
GID - Global Information Distribution
GNS - Get Nearest Server
--- H ---
HSSI - High-Speed Serial Interface
HTML - HyperText Markup Language
HTTP - Hypertext Transfer Protocol
HTTPS - Hypertext Transfer Protocol Secure
--- I ---
IANA - Internet Assigned Numbers Authority
IAP - Internet Access Provider
IAB - Internet Architecture Board
ICMP - Internet Control Message Protocol
IDRP - Inter-Domain Routing Protocol
IEEE - Institute of Electrical and Electronics Engineers
IESG - Internet Engineering Steering Group
IETF - Internet Engineering Task Force
IGMP - Internet Group Management Protocol
IGP - Interior Gateway Protocol
InARP - Inverse Address Resolution Protocol
IP - Internet Protocol
IPX - Intergrated Packet Exchange
IPX/SPX - Intergrated Packet Exchange/Sequenced Packet Exchange
IRC - Internet Relay Chat
IRTF - Internet Research Task Force
ISDN - Integrated Services Digital Network
ISO - International Standards Organization
ISP - Internet Service Provider
IDSL - ISDN Digital Subscriber Line
IMAP - Internet Message Access Protocol
ISDN - Integrated Services Digital Network
--- J ---
JUNET - Japan UNIX Network
--- K ---
Kbps - Kilobits Per Second
KBps - KiloBytes per second
--- L ---
LAN - Local Area Network
LANE - Local Area Network Emulation
LDAP - Lightweight Directory Access Protocol
LLC - Logical Link Control
--- M ---
MAC - Media Access Control
MAN - Metropolitan Area Network
MAU - Multistation Access Unit
MBps - Megabytes Per Second
Mbps - Megabits Per Second
MIB - Management Information Base
MIME - Multiple Internet Mail Extensions
Modem - Modulate/Demodulate
MRU - Maximum Receive Unit
MTU - Maximum Transmissionn Agent
--- N ---
NAS - Network Attached Storage
NAT - Network Address Translation
NCP - Netware Core Protocol
NDIS - Network Driver Interface Specification
NDP - Neighbor Discovery Protocol
NDS - Novell Directory Services
NetBEUI - NetBIOS Extended User Interface
NetBIOS - Network Basic Input/Output System
NFS - Network File System
NIC - Network Interface Card
NNTP - Network News Transfer Protocol
NTP - Network Time Protocol
NVT - Network Virtual Terminal
--- O ---
ODI - Open Data-link Interface
OSI - Open System Interconnect
OSPF - Open Shortest Path First
--- P ---
P2P - Peer to Peer
PAD - Packet Assembler/Disassembler
PAN - Personal Area Network
PAT - Port Address Translation
Pb - Peta byte
PDU - Protocol Data Unit
PEP - Packet Exchange Protocol
PING - Packet InterNet Groper
POP - Post Office Protocol
POTS - Plain Old Telephone System
PPP - Point to Point Protocol
PPPoA - Point-to-Point Protocol over ATM
PPPoE - Point-to-Point Protocol over Ethernet
PPTP - Point to Point Tunneling Protocol
PSDN - Packet Switched Data Network
PSTN - Public Switched Telephone Network
PVC - Permanent Virtual Circuit
--- Q ---
QoS - Quality of Service
QoSP - Quality of Service Parameters
--- R ---
RARP - Reverse Address Resolution Protocol
RBCS - Remote Boot and Configuration Service
RFC - Request for Comment
RIP - Routing Information Protocol
RPC - Remote Procedure Call
--- S ---
SAN - Storage Area Network
SATAN - Security Analysis Tool for Auditing Networks
SLIP - Serial Line Internet Protocol
SMTP - Simple Mail Transfer Protocol
S/N - Subnet
SNA - Systems Network Architechture
SNAP - Sub-Network Access Protocol
SNMP - Simple Network Management Protocol
SNTP - Simple Network Time Protocol
SPX - Sequenced Packet Exchange
SQL - Structure Query Language
STP - Shieled Twisted Pair
SSH - Secure Shell
SSL - Secure Socket Layer
SVC - Switched Virtual Circuit
SWAT - Samba Administration Tool
--- T ---
TB - Terabytes
TBps - Terabytes per second
Tbps - Terabits per second
TCP - Transmission Control Protocol
TCP/IP - Transmission Control Protocol/Internet Protocol
TFTP - Trivial File Transfer Protocol
TOS - Type Of Service
TTL - Time To Live
--- U ---
UDLC - Universal Data Link Control
UDP - User Datagram Protocol
UNC - Universal Naming Convention
URL - Uniform Resource Locator
UTP - Unshieled Twisted Pair
UUEncode - Unix to Unix Encoding
--- V ---
VBR - Variable Bit Rate
VPC - Virtual Path Connection
VPN - Virtual Private Network
--- W ---
WAN - Wide Area Network
WANG - Wide Area Network Group
WINS - Windows Internet Naming Service
WLAN - Wireless Local Area Network
--- X ---
XDR - External Data Representation
xDSL - Extended Digital Subscriber Line
XML - Extensible Markup Language
XSL - Extensible Stylesheet Language
XSML - Extensible Stylesheet Markup Language
--- Y ---
--- Z ---
ZCS - Zero Code Suppression
^ The above information was copied from http://www.xtremetek.com/info/index.php?id=2&page=1#o
If you happen to notice one missing, please email it to me at Admin@remedycomputing.com
Common Cisco Symbols and Basic Network Topologies
Below are pictures of common Cisco symbols and basic logical network topologies. It is important that you are familiar with the Cisco icons [which can also be found using the Cisco Packet Tracer program provided by the Cisco Academy] and understand the advantages/limitations of each common network topology.
^ http://whatis.techtarget.com/definition/network-topologies.html
^ Taken from the Cisco Academy CCNA coursework, 1.3.2.2
^ http://whatis.techtarget.com/definition/network-topologies.html
^ Taken from the Cisco Academy CCNA coursework, 1.3.2.2
General Troubleshooting
Today, I worked on a system that was heavily infected. After a tedious removal precess, I was left with corrupt Windows Vista operating system files. To fix this, I first tried running System File Checker at the command prompt [Start>Run>"cmd">"sfc /scannow"] but received a message stating that SFC was unable to repair all errors. So, I ran a Repair Install by running [in Windows] the Windows Installation Disc that matched the version of Vista that was already installed, choosing the Upgrade option and allowing it to download the latest files for installation. Once this finished, I checked to make sure the repairs were made correctly by running SFC again, but with a different switch, "sfc /verifyonly". Fortunately, everything went well and the operating system files were fixed but I still had one more issue; every time I would close a Windows Explorer [not Internet Explorer] window, I would receive an error saying "Windows Explorer has stopped working...blah blah" and then it would restart Windows Explorer [not to be confused with rebooting the operating system]. Of course, I couldn't release this to a customer in its current condition, so I dug a little deeper into the error. The error window had an arrow that showed that the message could be expanded to view more information. The other information provided pointed to a file called "facesmoochAU.dll". I searched for the file and opened the folder where it was located. Inside this folder, there was only 1 other file, that appeared to be some sort of configuration data. I opened the file in Notepad and saw that it was actually part of a toolbar in Internet Explorer, a program that I wasn't even trying to run, so I uninstalled the toolbar and restarted the system. BAM! No more errors.
You may not have this exact issue, but the troubleshooting process here is one that could be applied to any number of issues. Hope it helps!
You may not have this exact issue, but the troubleshooting process here is one that could be applied to any number of issues. Hope it helps!
Sunday, September 4, 2011
MSPaint Hex Hack
Little tricks like opening a command prompt using MSPaint are things that I find useful.
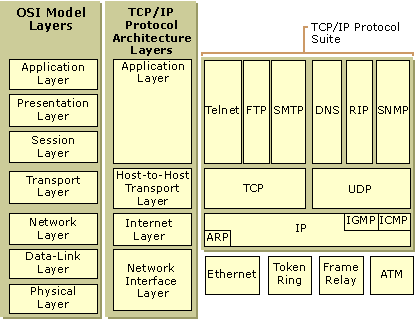
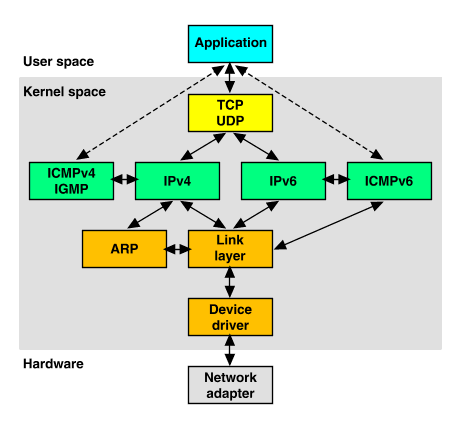
TCP/IP and Encapsulation
For those beginning their CCNA courses, understanding the process data goes through from end to end is important. More info to come.
^ http://www.softpanorama.org/Net/tcp_protocol_layers.shtml
^ http://en.wikipedia.org/wiki/TCP/IP_model
^ http://uw713doc.sco.com/en/NET_tcpip/tcpN.tcpip_stack.html
^ http://www.softpanorama.org/Net/tcp_protocol_layers.shtml
^ http://en.wikipedia.org/wiki/TCP/IP_model
^ http://uw713doc.sco.com/en/NET_tcpip/tcpN.tcpip_stack.html
Subscribe to:
Posts (Atom)